SSH Keys With Foxpass
What is an SSH Key?
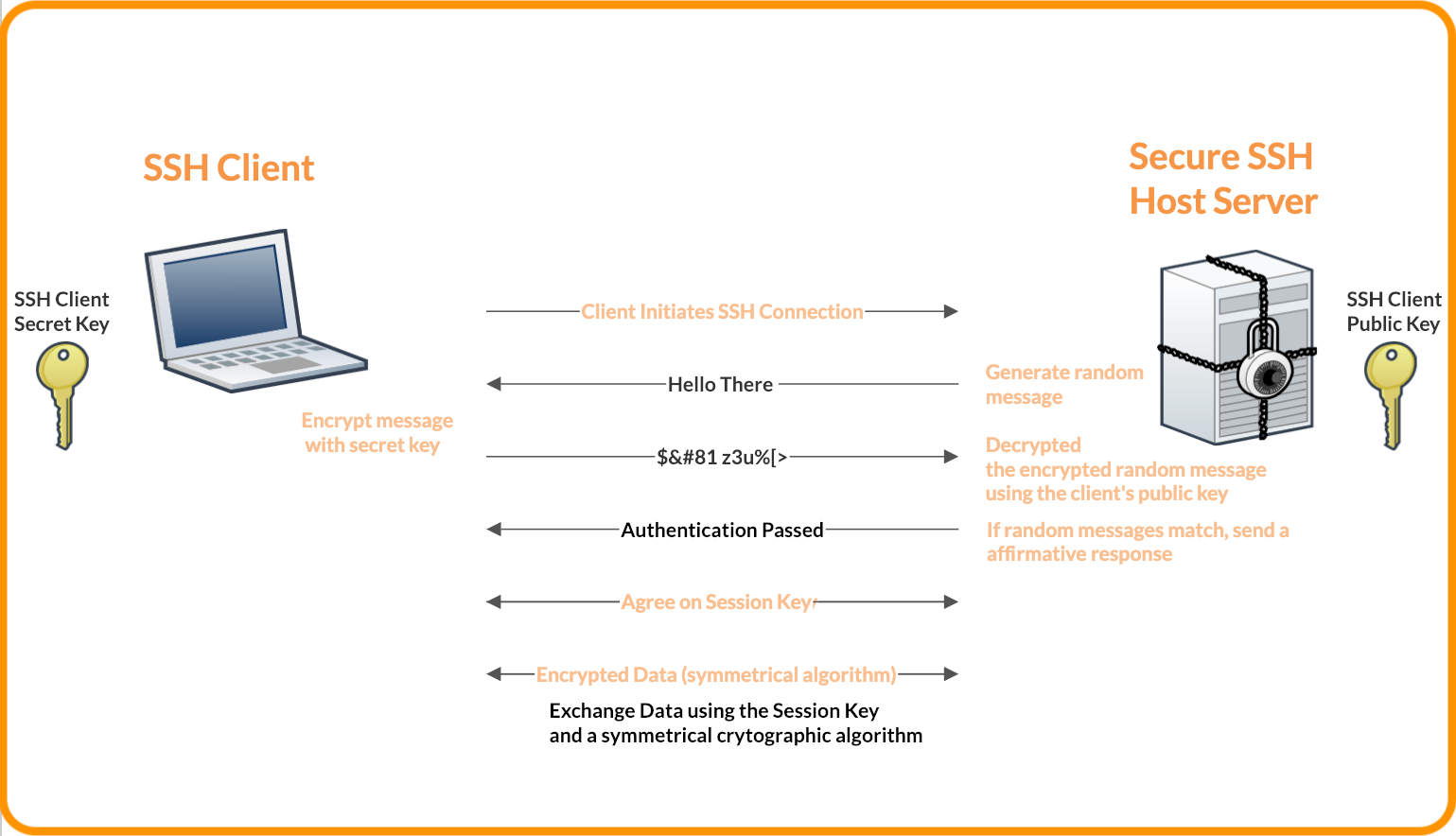
SSH keys serve as an alternative to traditional usernames and passwords, revolutionizing user authentication methods. Unlike conventional text-based passwords, SSH keys involve the presentation of an encrypted file to the service.
The exchange of access credentials via SSH keys occurs within the Secure Shell protocol, a secure substitute for the inherently vulnerable Telnet. Employing cryptographic techniques, SSH keys establish an encrypted conduit for all communication between the client and the remote server.
Beyond authenticating a remote user's identity, this approach also enables the smooth transmission of inputs from the client to the host, culminating in the relay of output back to the client. Practically speaking, each user generates their unique SSH key pair, retaining the private portion on their local machine while deploying the public counterpart on servers where access is required.
How are SSH Keys Used?
SSH keys find their primary purpose in facilitating access to Linux servers, which play a pivotal role in driving the majority of websites and applications.
Constant engagement with these servers is a necessity for software engineers, enabling them to execute tasks such as code deployment, bug rectification, and configuration adjustments.
A Manual SSH Key Management Alternative is Foxpass
Experience unparalleled ease and top-tier security in SSH key management and server protection through Foxpass.
Among the numerous offerings, this stands as a shining example of Foxpass's capability to deliver enterprise-grade security without straining your budget.
For More Information Visit Now:
https://www.foxpass.com/blog/l....earn-ssh-keys-in-min